Welcome to Definition Monday, where we define and explain a common technology or security concept for the benefit of our less experienced readers. This week: Virtual Private Networks.
Virtual Private Networks, commonly referred to as “VPNs” for the sake of brevity, are a common technology in today’s corporate networks. The concept behind them is simple – provide a way for two geographically distinct sites to appear to be on the same internal LAN, so that the users and computers on those networks can share resources. At the same time, of course, those resources need to be protected from the users of the Internet at large.
Back in the Dark Ages, when I started working in IT, connecting two sites to one another required either either laying fresh cable or (more likely) leasing a connection from the local telecom monopoly. You would call up the corporate sales office for your RBOC and tell them that you needed a T-1 or T-3 or Frame Relay connection between two sites, and they would quote you an outrageous price. You would then pay it, because you had no other options, and would receive a slow-by-today’s-standards dedicated connection between the two locations. Your satellite office could now access internal resources in your main office.
Now, dedicated lines weren’t all bad, of course – they were reliable, for the most part, and secure. But they were very pricey, and not a geographically flexible technology; if you signed that contract, your satellite office wasn’t going to be moving for a long, long time.
VPNs give that same sort of functionality, but without the physical networking path. Essentially, a VPN is a cryptographically secure tunnel between two sites on the Internet. Traffic flows through, from one side to the other, securely wrapped in something like IPsec and unaware of the transition between networks. From the point of view of the end user’s applications, it is a transparent technology.
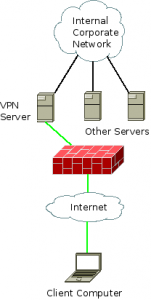
One implementation style of VPN is the client-server model, as seen above: this is when a remote worker needs to access corporate resources, and so he or she runs a VPN software client on a computer at a remote location to connect to the corporate network. This allows the client to have a network address on the corporate network; it’s essentially the same as just giving the client a very, very long Ethernet cable and plugging it in behind the corporate firewall. All traffic intended for the corporate network, symbolized by the green line above, passes through the firewall and is able to access the internal corporate network directly.
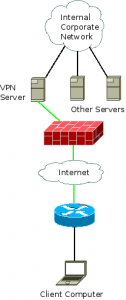
Another style is the site-to-site, or LAN-to-LAN, model. This is the replacement for the dedicated leased line model above; traffic is transparently routed through a tunnel between the edge of one network and the VPN concentrator on another network. Using the same green line as in the previous example, you see that the encrypted tunnel actually starts at the router that the client computer is connected to, rather than at the client computer itself. This would be used when setting up a remote or satellite office. But since the VPN is not tied to a physical wiring structure, as with a leased line, this can be used to set up a temporary office “in the field”.
Which approach is correct? It depends on a lot of factors – how many people will be using the VPN, how permanent a satellite location is, what sort of authentication and authorization schemes you have in place or need to be implemented. But independent of the details, the VPN technology as a whole is an excellent tool for a geographically dispersed business that needs to share computer resources among employees while protecting them from the Internet at large.



 Posted by matt
Posted by matt 
